Why you can trust TechRadar
We spend hours testing every product or service we review, so you can be sure you’re buying the best. Find out more about how we test.
This review first appeared in issue 359 of PC Pro.
Acronis’ Cyber Protect teams up hybrid backup services with full-strength cybersecurity and endpoint protection. One subscription takes care of everything, and it’s all managed from a single cloud portal.
Cyber Protect 16 Advanced takes the Standard edition and adds features such as Windows patch management, backup malware scans and an endpoint detection and remediation (EDR) service that provides event correlation, threat containment, incident investigation, kill chain analysis and endpoint rollback recovery. Ransomware protection comes with tamper-proof immutable backups and a compliance mode that stops malicious actors from changing account settings and deleting backups.
There are a lot of activities to keep track of, but the cloud portal helps by presenting a customizable dashboard. You have lots of widgets to choose from, including ones for protected system overviews, backup storage usage, vulnerable systems, alerts, detected malware, patch remediation status and blocked website categories.
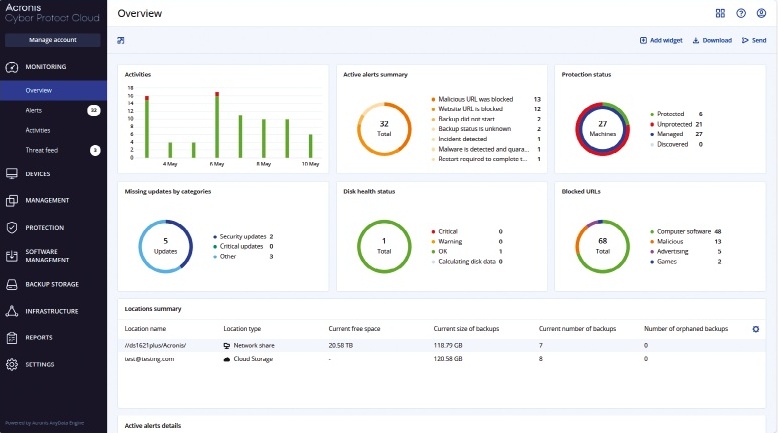
Platform support is outstanding and includes Windows, macOS and Linux systems, iOS and Android mobiles, many popular business apps, ten virtualization hosts, and cloud apps such as Microsoft 365 and Google Workspace. Agent deployment for workstations and servers is a lengthy affair, though, as they must be downloaded from the portal and manually installed, after which they generate a unique registration code and appear in the portal’s devices page.
Hyper-V virtual machine (VM) backups require a dedicated agent installed on the host, and you now have two choices for VMware systems. You can install an agent VM directly on the host and register it with your cloud account or use the new Windows remote agent.
Applying settings is much simpler. You place similar systems in groups and assign protection plans that include your backup settings, encryption passwords, schedules and all cybersecurity settings. For hybrid backups, primary and secondary storage locations can be assigned. We used local Synology NAS shares for fast local backups and the Acronis cloud repository for off-site storage.
Synology NAS appliances can now be protected by a DSM agent app. It temporarily needed root access to register with our Acronis account, and we could then access the appliance from the cloud portal, create a protection plan and choose the shares we wanted backed up to the cloud.
Along with swift file and folder recovery services for remote servers and workstations, the portal provides an impressive range of restore features for Hyper-V and VMware. You can recover an entire VM back to its original location, as a new VM on the same host or another one. For even faster recovery, a temporary VM can be created on the host from a local backup.
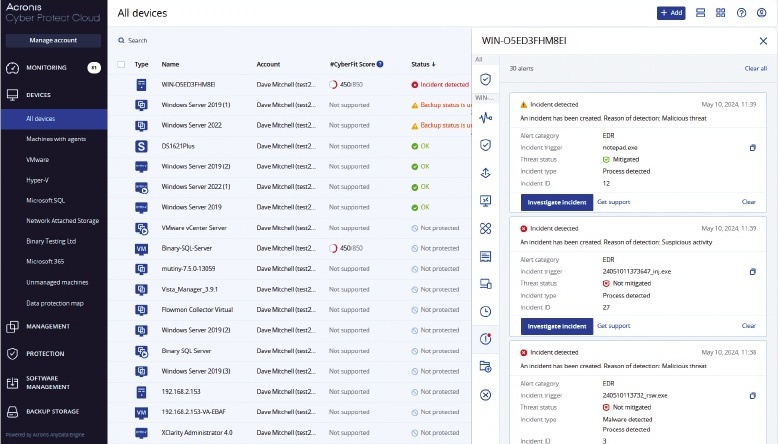
Within workstation and server plans, you can enable real-time malware scanning, apply URL filtering using up to 44 categories, schedule vulnerability assessments, run patch management remediation tasks and enforce removable device controls. When EDR is activated, you can view all incoming alerts from the portal, see lists of all incidents filtered by severity and mitigation status and browse a threat investigation page which provides a kill chain diagram, details of how the attack developed and the processes it interacted with.
Businesses that want all their data backup and cybersecurity in one place will love Acronis Cyber Protect 16 Advanced. Its flexible subscriptions keep costs under control, the EDR service stays one step ahead of cybercriminals and it’s easy to manage.
We also ranked the best free backup software.
Probably the most respected tester of IT equipment in the UK, if you’ve bought a piece of kit for the office – whether printer, server or rack appliance – then you’ve probably read Dave’s verdict at some point along the way.
What is a hands on review?
Hands on reviews’ are a journalist’s first impressions of a piece of kit based on spending some time with it. It may be just a few moments, or a few hours. The important thing is we have been able to play with it ourselves and can give you some sense of what it’s like to use, even if it’s only an embryonic view. For more information, see TechRadar’s Reviews Guarantee.

Microsoft announces its own Black Hat-like hacking event with big rewards for AI security
Dangerous global botnet fueling residential proxies is being hit in major crackdown

Why VMWare’s legacy strengths no longer justify its modern complexities
Most Popular











-
 1Google is giving Gemini AI a memory for your favorite things
1Google is giving Gemini AI a memory for your favorite things -
2Quordle today – hints and answers for Thursday, November 21 (game #1032)
-
3NYT Connections today — hints and answers for Thursday, November 21 (game #529)
-
4NYT Strands today — hints, answers and spangram for Thursday, November 21 (game #263)
-
5Meta AI smart glasses say bonjour, hola, and ciao to Europe and new languages



